Compliance and cyber insurance
1Password helps by mitigating credential risks, enforcing device compliance, and giving you compliance visibility and management of your application access privileges.

The impact of non-compliance
Failing to meet compliance standards exposes businesses to data breaches, regulatory penalties, or being unable to operate in some industries or serve some customers.
Ransomware risks
In more than 92% of cases where attacks progressed to ransom stage, the attacker had leveraged unmanaged devices in the network.
Source: Microsoft Digital Defense Report, Microsoft Threat Intelligence, October 2024.
Non-compliance costs
There’s been more than $5.3 billion in total GDPR fines as of October 2024.
Source: GDPR Enforcement Tracker, October 2024.
Data breaches
68% of breaches involved a human element such as compromised user credentials or phishing.
Source: Verizon Data Breach Report, May 2024
Navigate the complexity of cybersecurity compliance
Credential risk management
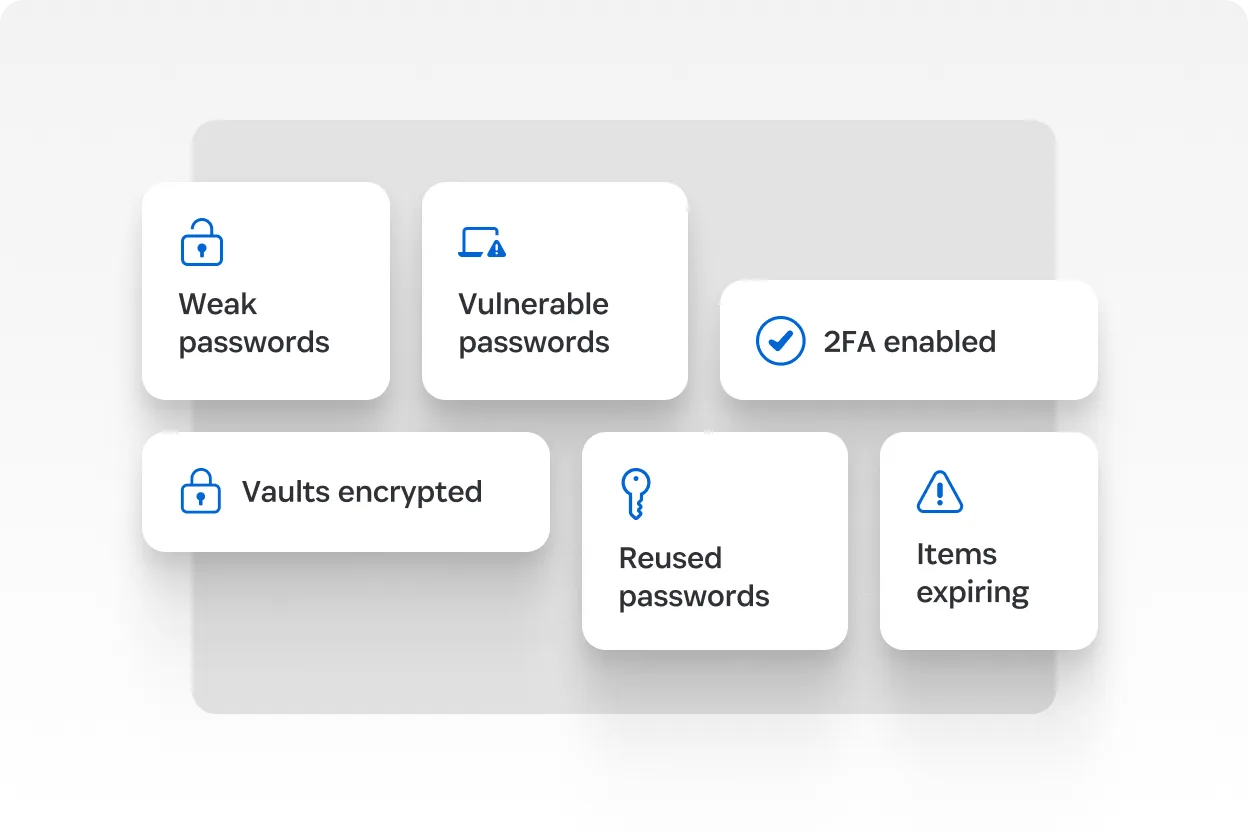
Device compliance enforcement
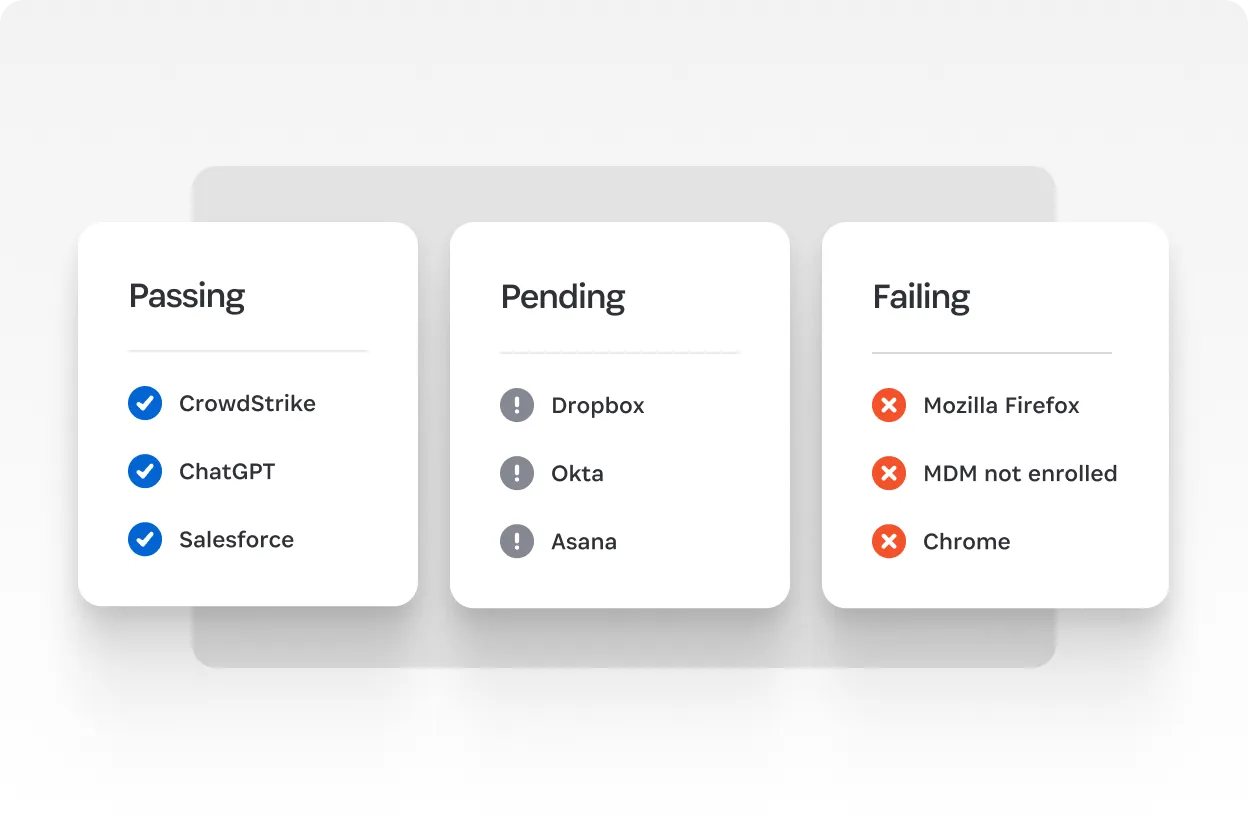
SaaS security and visibility
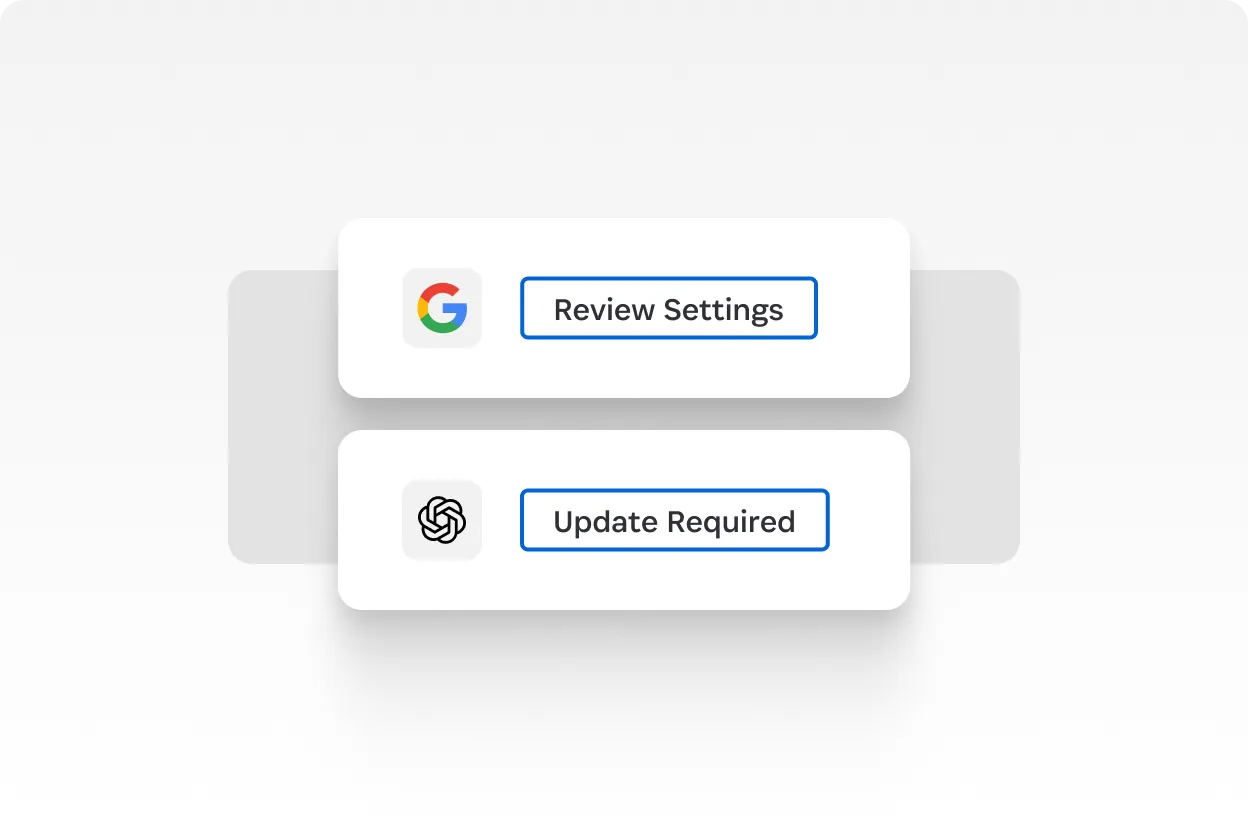
Meet cyber compliance and insurance standards
Safeguard sensitive data and protect against ransomware threats with the only platform that combines credential risk management, device trust, and secure access to SaaS.
Secure every sign-in

Store all sign-ins in secure vaults, with the ability to securely share passkeys, strong passwords, secrets, and more.
To every application

Manage access to every application and web account for your workforce.
From any device

Sign in to everything from secure devices, and set policies to ensure only healthy and trusted devices access applications.
Close the Access-Trust Gap
Traditional cybersecurity tools are not enough to meet the demands of a modern workforce.
Granular access controls
Add custom groups based on department roles or functions and apply permissions based on those job functions.
Multi-factor authentication (MFA)
Add strong, unique passwords, passkeys or MFA where SSO doesn’t cover sign-ins.
Contextual access policies
Allow or block sign-ins based on device compliance at the time of login.
Access reviews
Standardize access reviews with comprehensive coverage across your SaaS stack.
Comprehensive audit trails
Track and log every credential, device, and app access event to ensure compliance.
Advanced encryption
Track and log every credential, device, and app access event to ensure compliance.


"Being able to track and trace (within limits) who accesses what, where, and how is a big deal, especially in reporting and auditing after the fact."
Lee Jon Scramstad
Systems Architect, Synex
180,000 businesses trust 1Password
Resources to kickstart your journey
More than compliance
Regulations are necessary, but security goes beyond merely meeting compliance requirements.
Simplify regulatory compliance
Simplify compliance cybersecurity risks with access controls, visibility, and auditing.
Extending access management
Why zero trust requires going beyond traditional IAM and MDM - and how to do it.
Solutions Guide: 1Password Extended Access Management
Fill critical gaps to secure the devices and applications that today’s tools cannot see.
Request a demo
See how 1Password helps your team meet compliance requirements with seamless, trusted access.
Frequently asked questions
What is cybersecurity compliance, and why does it matter?
Cybersecurity compliance refers to meeting regulatory requirements and cybersecurity frameworks designed to protect sensitive data and prevent breaches. ISO 27001, SOC 2, NIST, HIPAA, GDPR and DORA are cybersecurity regulations and frameworks that can help organizations implement controls to safeguard data, enforce access controls, and prevent data breaches.