Simplify Access Reviews
Use SaaS Manager's automated workflows to continuously and confidently review user access to apps.
Compliance made easy
Regularly verify who has access to apps, easily and securely, to prove compliance with standards including SOC 2, PCI, SOX, and ISO27002/27017.

Centralized Control
Manage access reviews in one place. Track progress and ensure reviewers follow standardized processes.

Clarity for auditors
Provide a detailed, exportable PDF audit trail of every access decision for auditors.

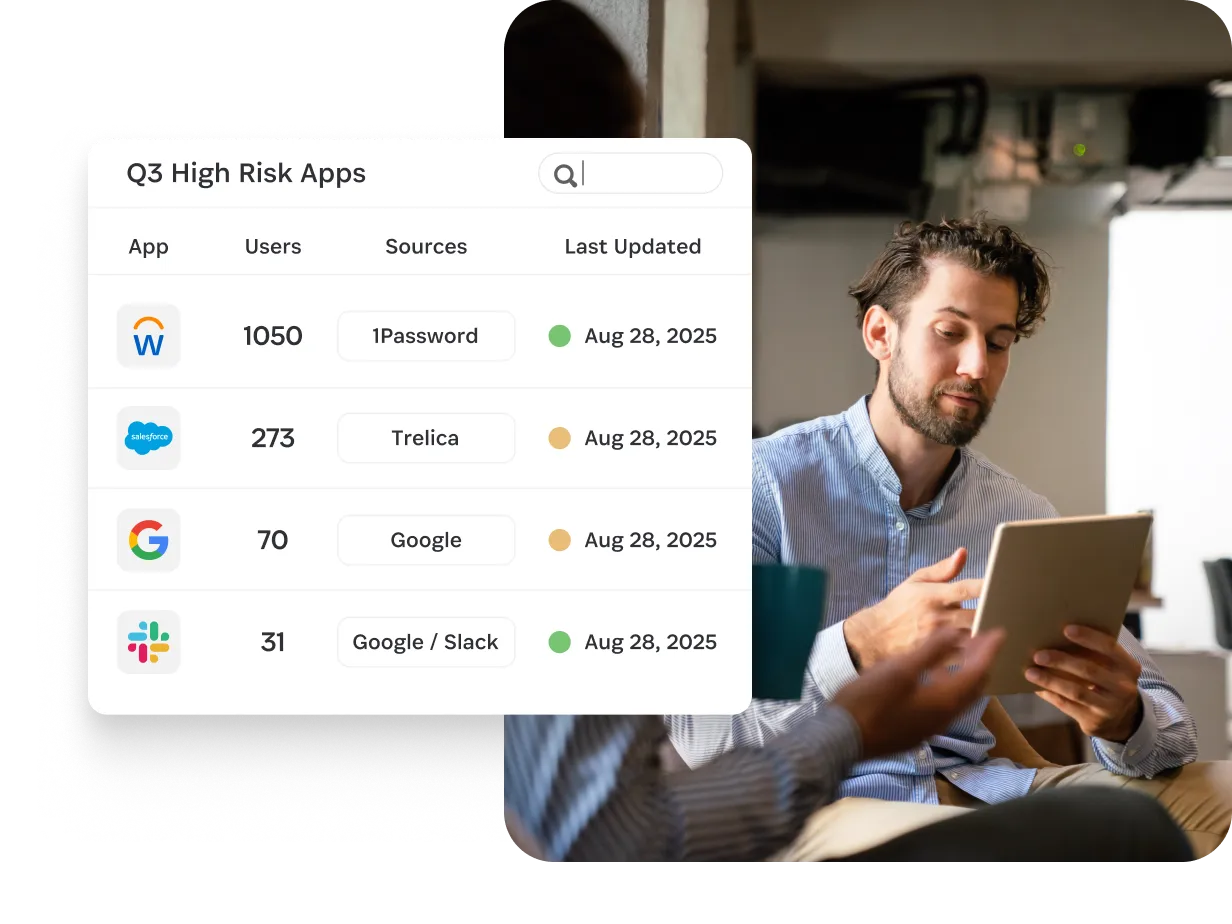
Complete coverage for apps
Review user access for every app, even when apps aren’t behind SSO or don’t support SCIM.
Comprehensive coverage for access reviews
Review user access to all apps in your environment in one place.
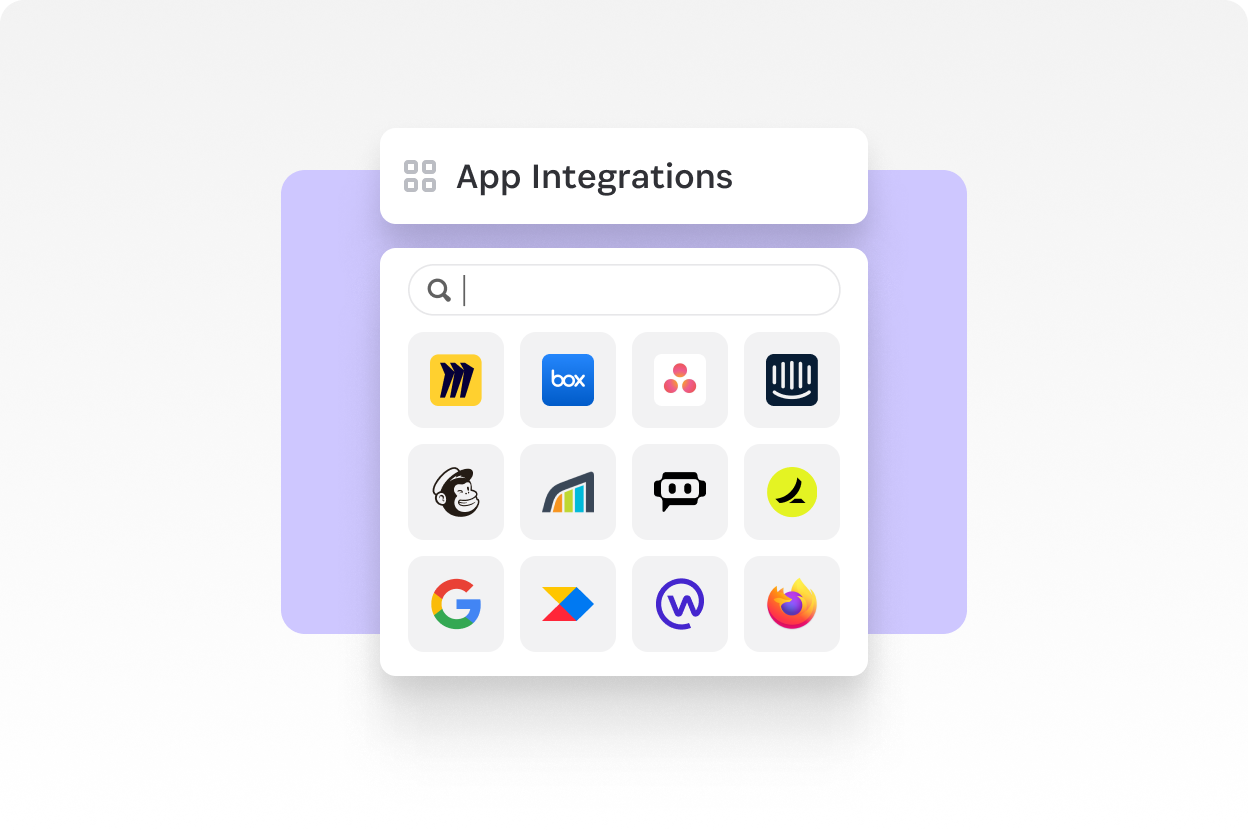
Integrate all your apps
Leave no app behind with SaaS Manager’s 350+ API integrations (no SCIM required), or utilize SaaS Manager’s API and CSV upload for custom apps.
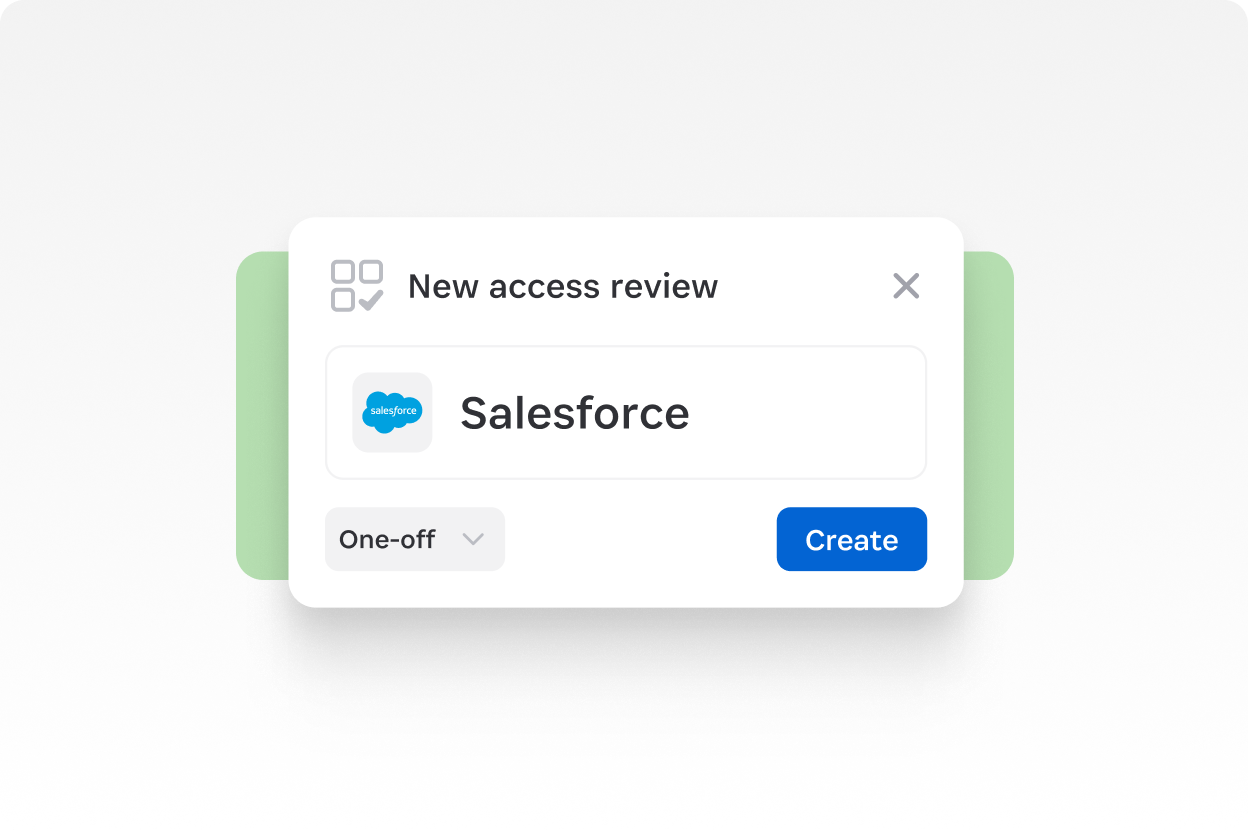
Set up one-off or recurring reviews
Select apps, assign app owners, and utilize automatic reminders so reviews don’t stall.
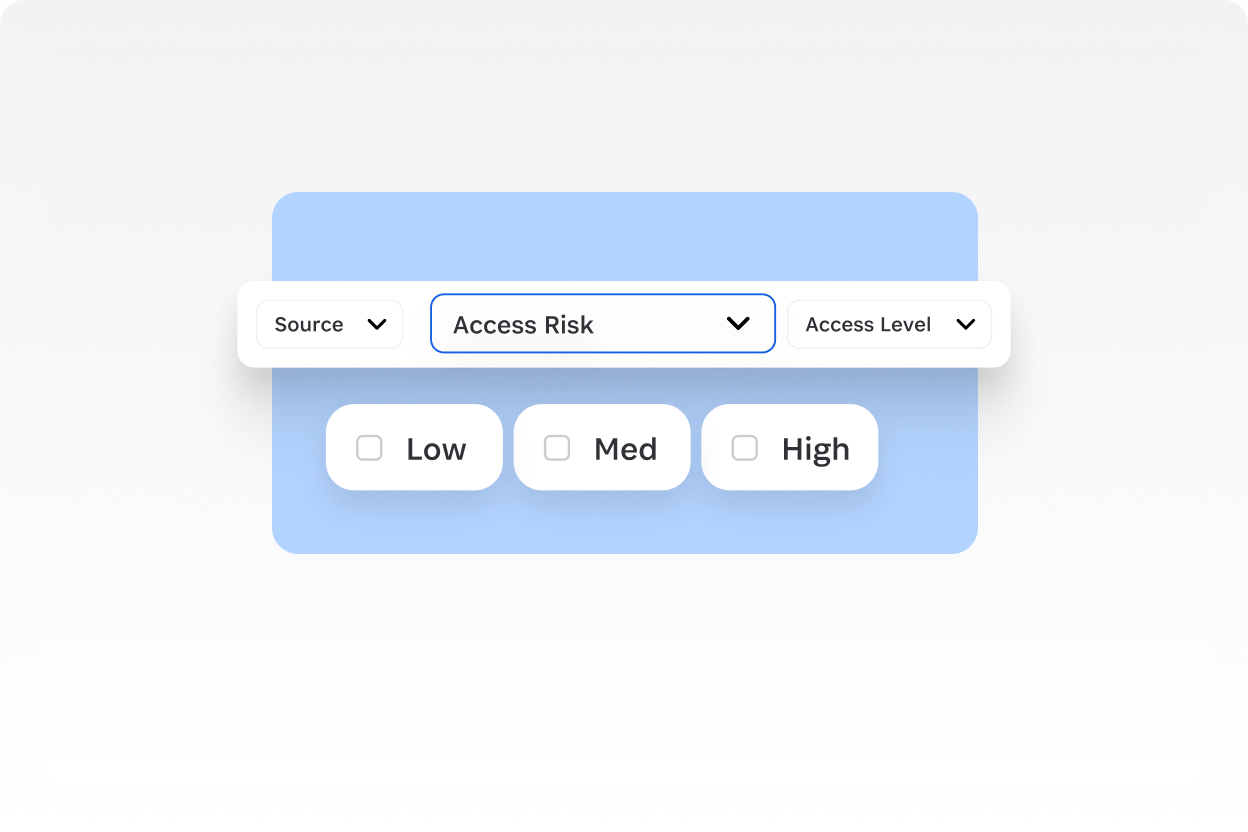
Surface critical details
Give reviewers the context they need to make informed access decisions, including access levels and access risks.
Filter for bulk editing
Filter by user role, access issue, or cost center and make bulk changes for faster reviews.
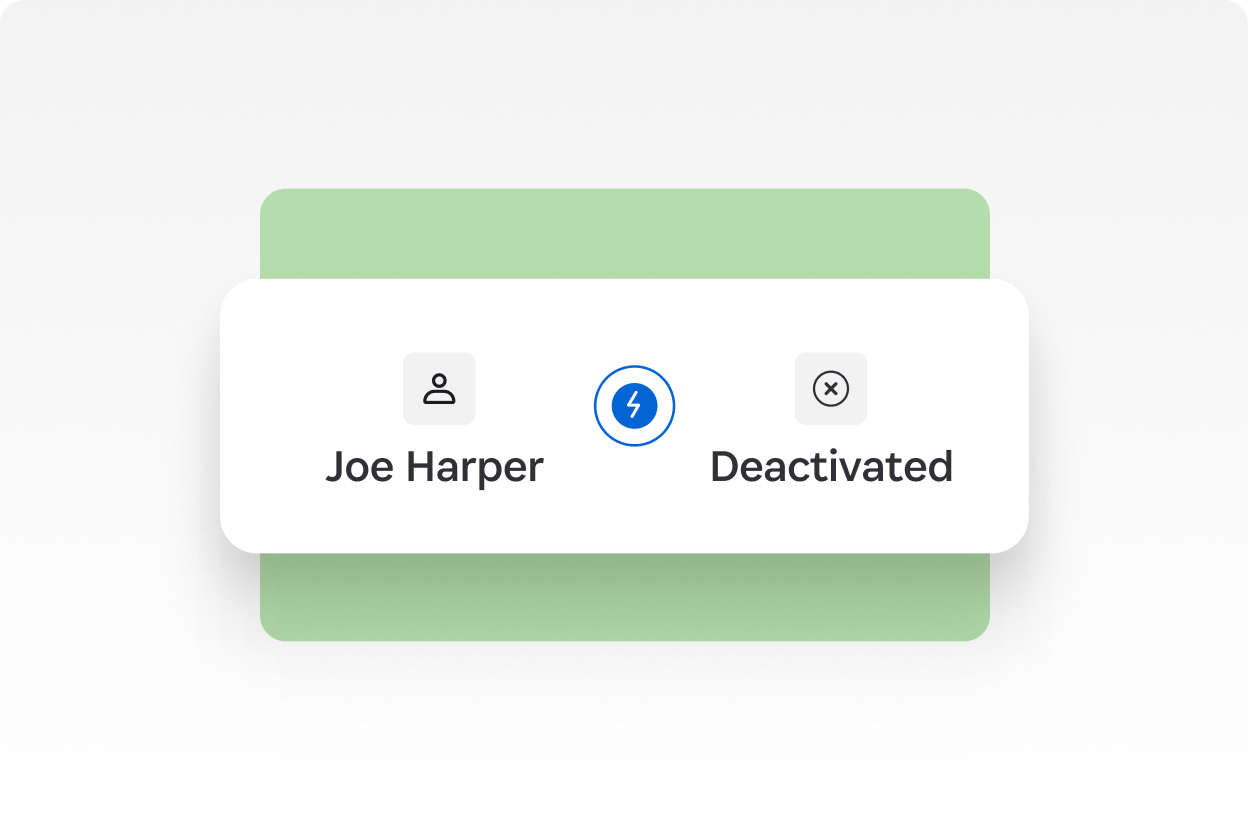
Revoke user access
Remove access to an app directly in access reviews, raise a SaaS Manager task synced with your ITSM, or record a manual action with notes.
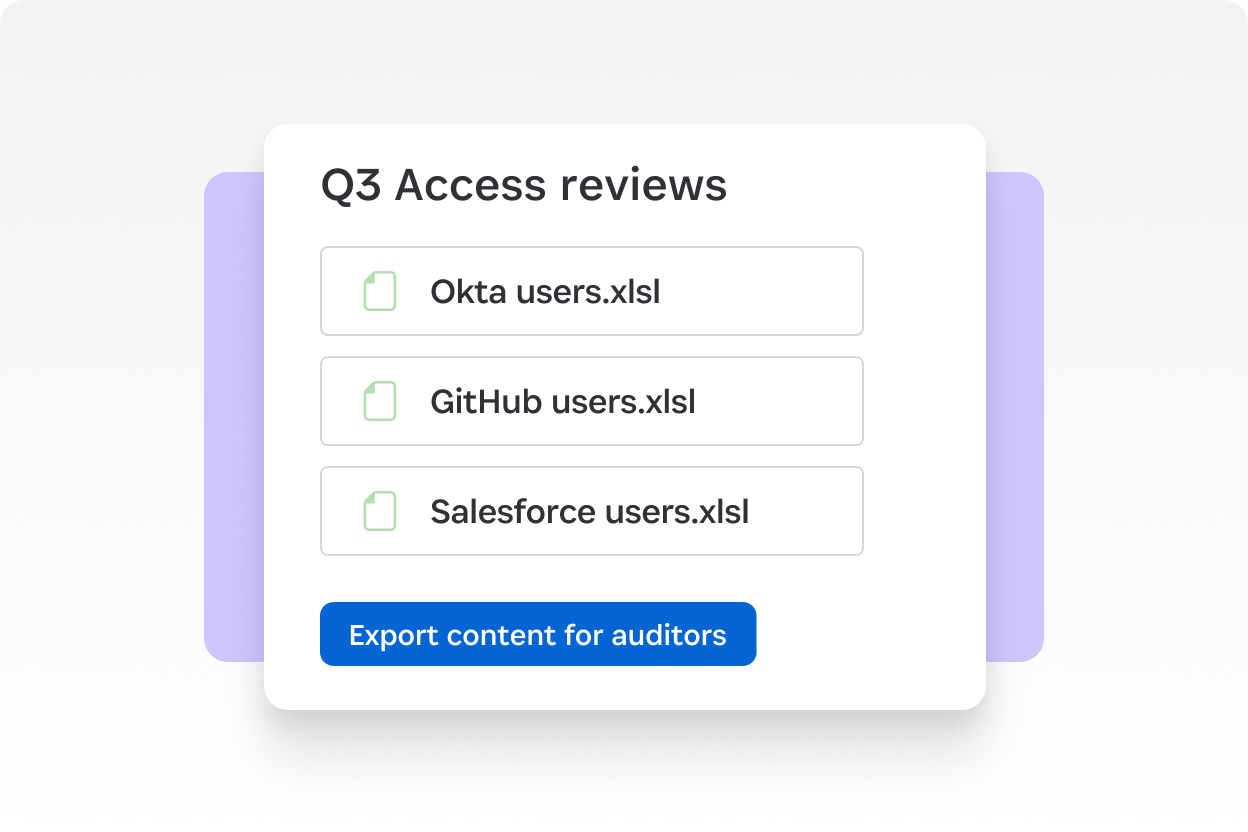
Export full context for auditors
Share a full audit trail of every access decision with supporting notes.
350+ App Integrations
Unify and simplify access reviews with a comprehensive library of app integrations.
Frequently asked questions
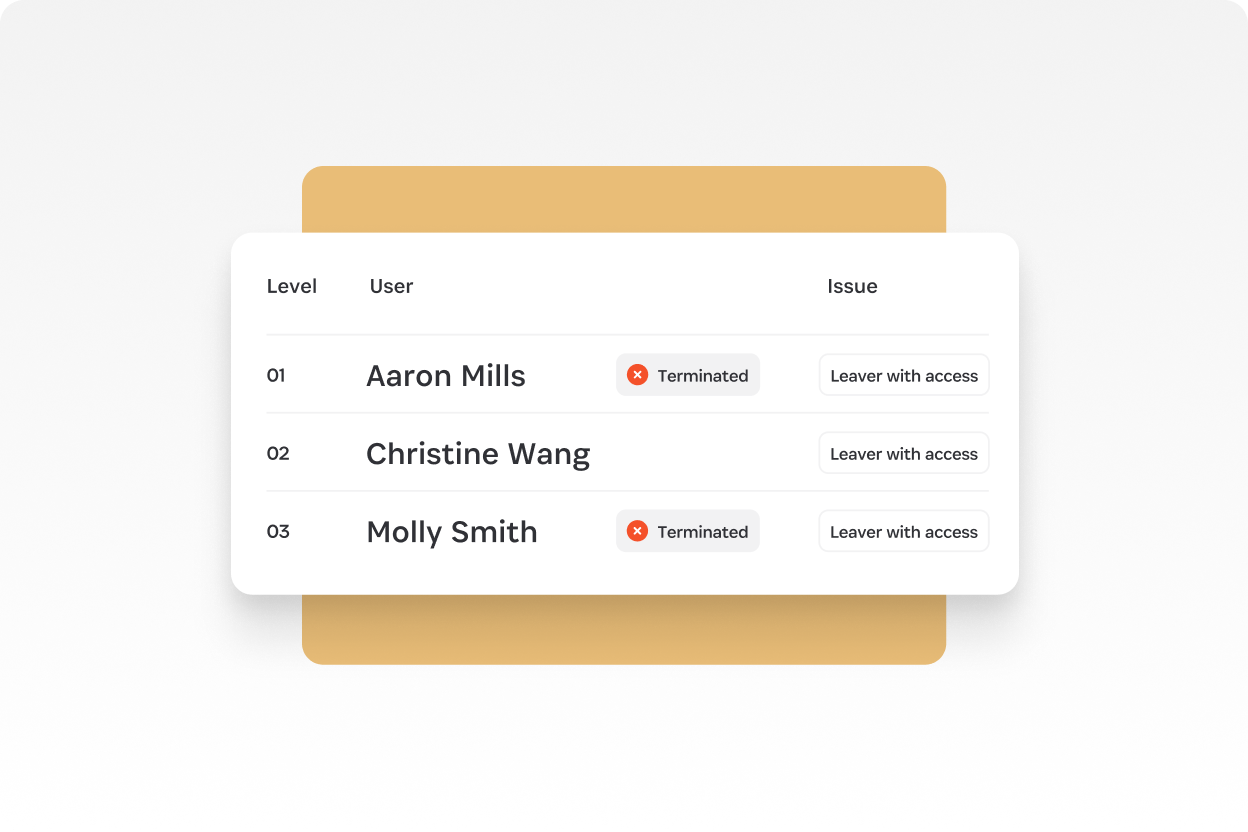
How do access reviews and offboarding workflows work together?
Access reviews serve as a critical check to ensure lifecycle management processes are working as intended. Access reviews catch users who still have access to apps when they shouldn't. For example, access reviews can identify leavers whose access should be revoked. With that insight, customers can set up automated offboarding workflows to reduce the risk of unauthorized access in the future.