Sécurisez toutes les connexions à chaque application depuis n'importe quel appareil
1Password Extended Access Management garantit que chaque identité est authentique, que chaque connexion à une application est sécurisée et que chaque appareil est sain. Simplifiez l’accès sécurisé aux applications pour les utilisateurs avec des connexions en un clic, tout en offrant aux équipes informatiques et de sécurité un contrôle centralisé, une visibilité et une application des politiques, sans compromettre l’ergonomie.
Combler le fossé entre accès et confiance laissé par les outils IAM et MDM traditionnels.
Alors que les organisations cherchent à équilibrer productivité et sécurité, elles font face à un fossé entre accès et confiance, c'est-à-dire aux risques de sécurité posés par des appareils, applications et outils alimentés par l'IA accédant aux données de l'entreprise sans contrôles de gouvernance adéquats. Les outils IAM, IGA et MDM traditionnels ne peuvent pas sécuriser toutes les applications, identités et appareils utilisés sur le lieu de travail en raison des environnements décentralisés modernes, axés sur les utilisateurs.
Des risques non gérés et non contrôlés

Des employés adoptent librement des outils de SaaS et d'IA non fédérés, ce qui aboutit à une décentralisation des accès et à des failles de sécurité. En l’absence de contrôle sur ces outils, les organisations font face à un risque accru de fuites, de non-conformité à la réglementation et d'inefficacités opérationnelles.
Les équipes informatiques et de sécurité contournées

Des appareils personnels et non gérés se connectent quotidiennement aux ressources des entreprises. En l’absente de contrôles adéquats, les risques pour la sécurité augmentent considérablement. Les données deviennent vulnérables et les actions ne sont pas toujours conformes à la réglementation.
Des connexions peu sécurisées et des accès non protégés

Lorsque des comptes et des agents d'IA sont utilisés sans être gérés, et lorsque certains modes d'authentification sont peu sécurisés, les organisations sont exposées à des risques, notamment en ce qui concerne les attaques par usurpation d'identifiants et les accès non autorisés. Dans ces conditions, la visibilité et le contrôle sont fragmentaires.
Accès sécurisé adapté au lieu de travail moderne
Sécurisez vos ouvertures de session
Gestionnaire de mots de passe pour les entreprises
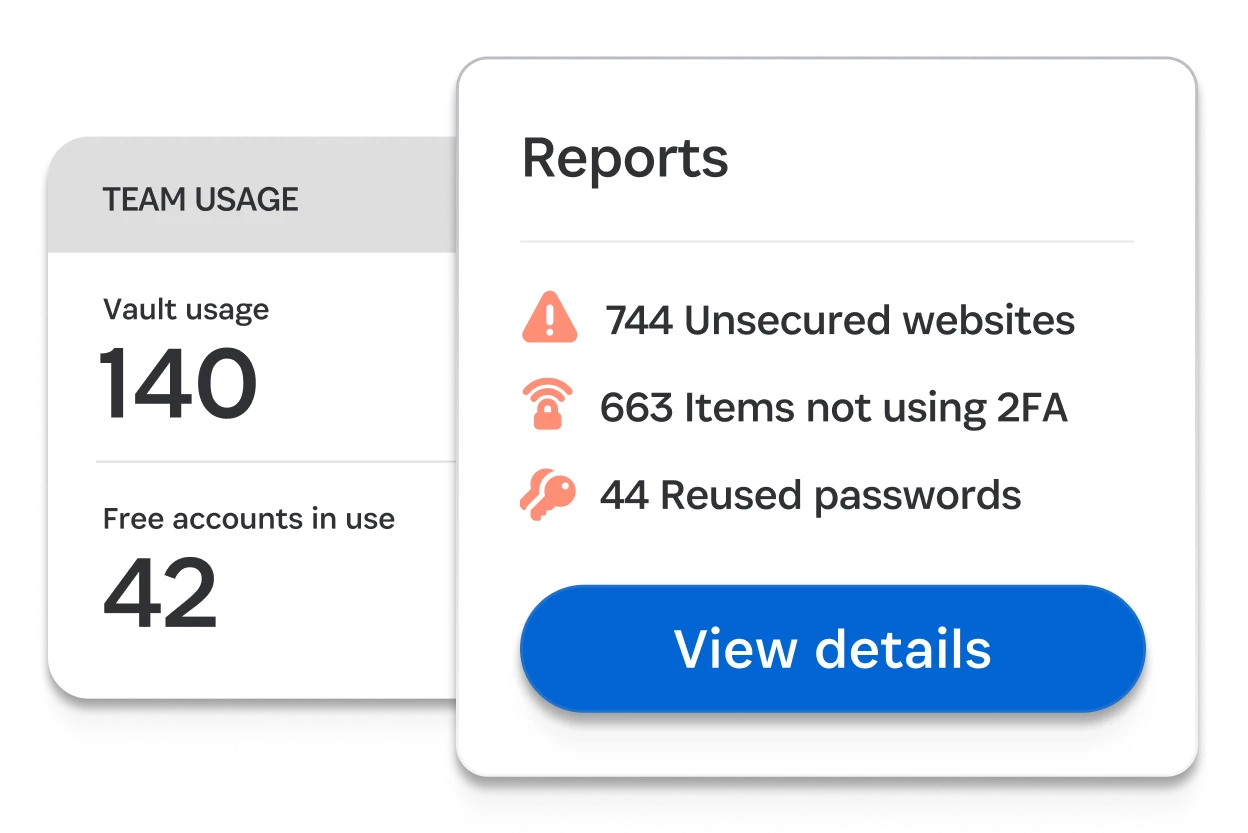
Sécurisez vos appareils
Device Trust de 1Password

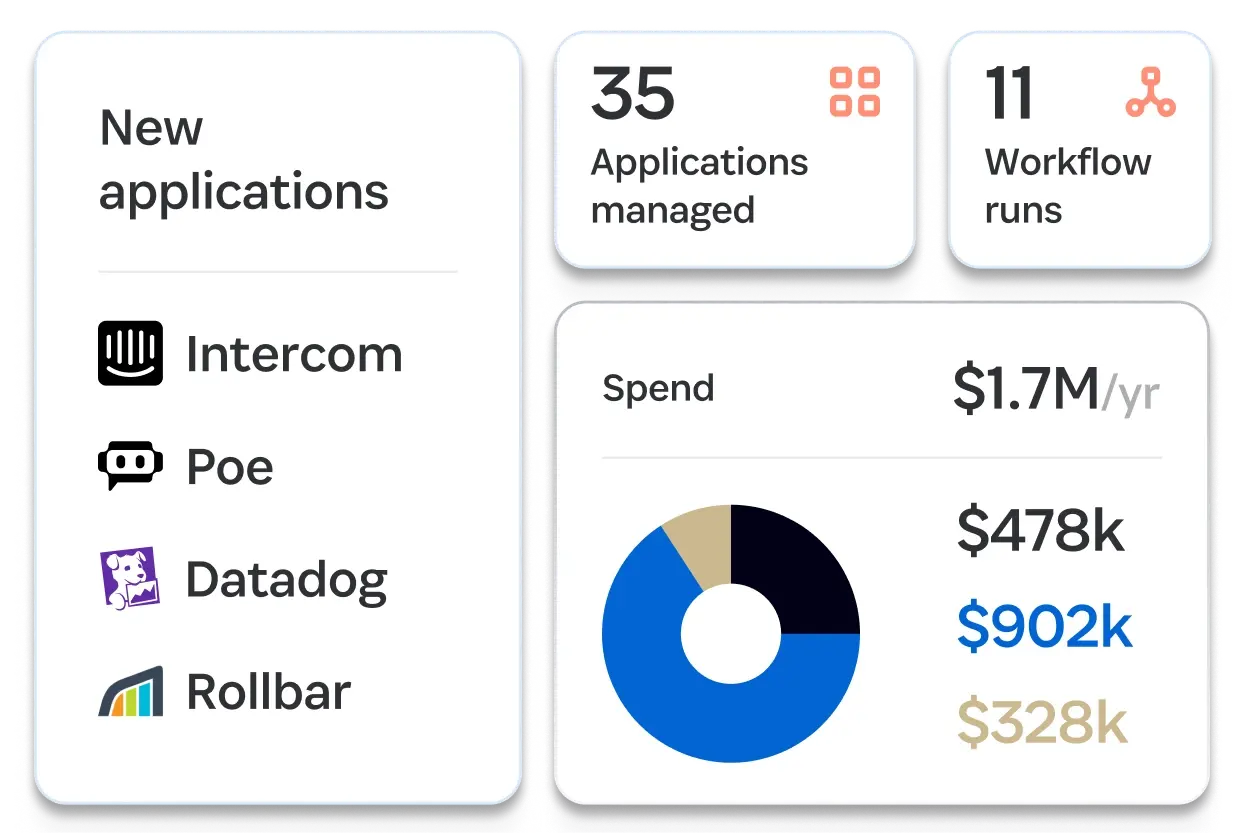
Sécurisez vos applications
SaaS Manager
Faites une visite guidée du produit
Découvrez l'approche fondamentalement différente de 1Password pour sécuriser chaque connexion, à chaque application, depuis chaque appareil.
Cette démonstration interactive a été masquée car elle nécessite des témoins de connexion que vous n’avez pas encore acceptés. Cliquez sur le bouton ci-dessous pour modifier vos préférences en rapport à ces témoins et lancer la démonstration interactive.
Sécurisez l'accès des agents humains et IA, sans ralentir les employés.
1Password Extended Access Management libère la productivité sans compromettre la sécurité. Éliminez les risques tout en offrant aux employés et aux agents d'IA la flexibilité et la liberté nécessaires pour accomplir leur travail.
Passez au sans mot de passe : gérez le risque lié aux identifiants.
Appliquez l'authentification la plus puissante possible pour chaque application, comme des informations d'identification uniques, MFA et des clés d'accès, et accélérez votre transition vers une expérience sans mot de passe.
Activez l'authentification sécurisée pour les agents d'IA
Accordez aux agents d'IA un accès sécurisé aux informations d'identification sensibles et au contexte privé, en éliminant les secrets codés en dur et l'accès permanent.
Bloquez les appareils inconnus et non sécurisés
Assurez-vous que seuls les appareils de confiance et conformes accèdent aux ressources de l'entreprise et permettez aux employés de résoudre eux-mêmes les problèmes de leurs appareils.
Gain visibility into shadow IT and all SaaS apps
Discover and manage SaaS, including shadow IT and shadow AI. Ensure each app meets compliance requirements.
Gérer l’accès aux services SaaS
Automatisez l'approbation des applications, gérez les événements du cycle de vie des utilisateurs comme l'intégration et le départ, et décidez qui peut accéder à quelles applications.
Préservez la conformité et les normes d’assurance cybernétique
Évaluez et atténuez les risques liés aux appareils, aux applications et aux informations d'identification, fournissez des rapports détaillés et une auditabilité, et éduquez les utilisateurs finaux sur les meilleures pratiques de sécurité.
180 000 entreprises et des millions de familles nous font confiance
Lancez-vous avec 1Password Extended Access Management
Découvrez comment 1Password Extended Access Management peut contribuer à optimiser la sécurité de chaque appareil, application et connexion. Demandez une démo pour commencer.
FAQ en rapport à 1Password Extended Access Management
Qu'est-ce que 1Password Extended Access Management ?
1Password Extended Access Management sécurise chaque connexion à chaque application depuis n'importe quel appareil, même les connexions non fédérées, les appareils non gérés et les applications difficiles à sécuriser avec les outils traditionnels de gestion des identités et des accès (IAM), d'authentification unique (SSO) et de gestion des appareils mobiles (MDM).